You might be shocked at how easy it is to obtain your personal login information, and you probably won’t know it’s happened until it’s too late. The dark web–that hidden corner of the internet–is teeming with stolen credentials. Hackers access compromised passwords through data breaches, phishing scams, and malware attacks, then put them up for sale to anyone willing to pay. This makes strong password management, including the use of secure passwords and two-factor authentication (2FA) more important than ever.
 Darci Creative
Darci Creative
Planning for the unexpected is a key part of IT management for every organization. A solid business continuity plan that includes a disaster recovery process and secure data backups can make the difference between bouncing back or shutting down in the face of a disruption. Why are these strategies so crucial? Image a scenario where a cyberattack suddenly halts your operations. Without a continuity plan in place, this could lead to lost data, costly downtime, and potential damage to your business’s reputation.
Municipalities face unique challenges when it comes to managing IT infrastructure. From safeguarding data to maintaining compliance with local and state regulations, effective IT management is necessary to ensure municipal operations run smoothly. Budget restrictions can make it difficult to fully staff an IT department that can meet the complex needs of schools, fire, police, planning, clerks, and more.
When a New Hampshire town became dissatisfied with their longtime IT vendor, they went looking for a second opinion. We were one of three managed service providers to submit a bid with remediation plans, and our bid was selected to become this municipality’s IT vendor. How did we create a custom proposal for their specific IT needs?
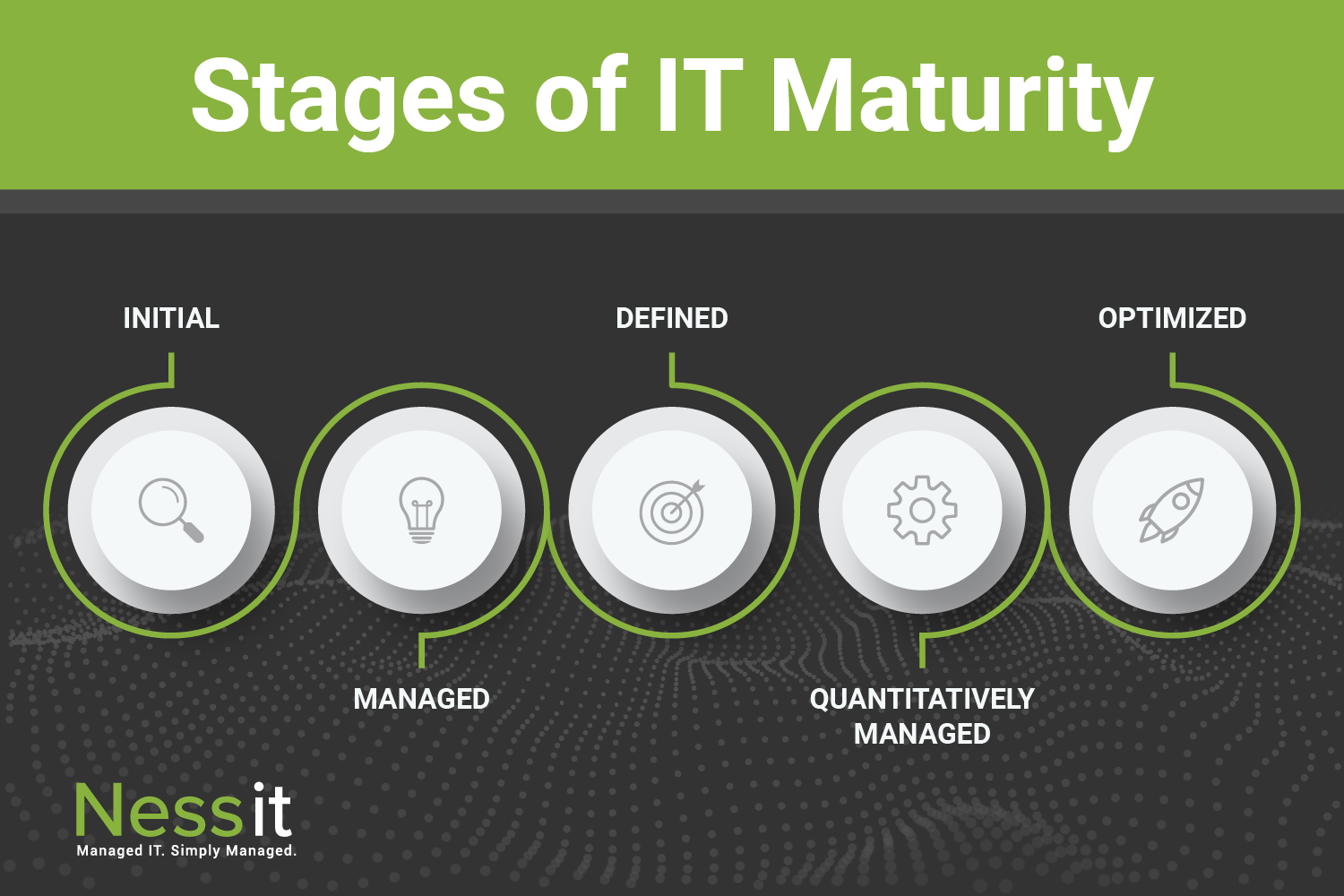
The effectiveness of your IT infrastructure greatly impacts the success of your business. Having basic IT systems in place is not enough. Achieving IT maturity is critical for long-term growth, innovation, and competitive advantage. So, what exactly is IT maturity, why is it important, and how can Nessit help your business get there?
The single most effective way to safeguard your business from cyberattacks is through employee training. Employees can unknowingly become the gateway for cybercriminals by clicking on malicious links, using weak passwords, falling for phishing scams, or accidentally sharing sensitive information that can compromise your entire network. Here’s what you need to know to protect sensitive data and maintain the integrity of your IT infrastructure:
Cybersecurity is a critical component in any organization, large or small. The increasing frequency and evolving nature of threats means that simply installing antivirus software or setting up a firewall isn’t enough. Security is an ongoing process that requires constant vigilance, regular updates, and proactive measures. As a Managed Service Provider (MSP), Nessit understands the complexities of maintaining robust cybersecurity and is dedicated to safeguarding your business.
Designing a cybersecurity program is complex, and expecting everyone within your organization to follow complicated policies is bound to fail. As with most things, simpler is better. At Nessit, experience has taught us that easy-to-understand cybersecurity policies are the most effective, and as cyber threats become more sophisticated, protecting sensitive data has never been more critical.