Municipalities face unique challenges when it comes to managing IT infrastructure. From safeguarding data to maintaining compliance with local and state regulations, effective IT management is necessary to ensure municipal operations run smoothly. Budget restrictions can make it difficult to fully staff an IT department that can meet the complex needs of schools, fire, police, planning, clerks, and more.
 Darci Creative
Darci Creative
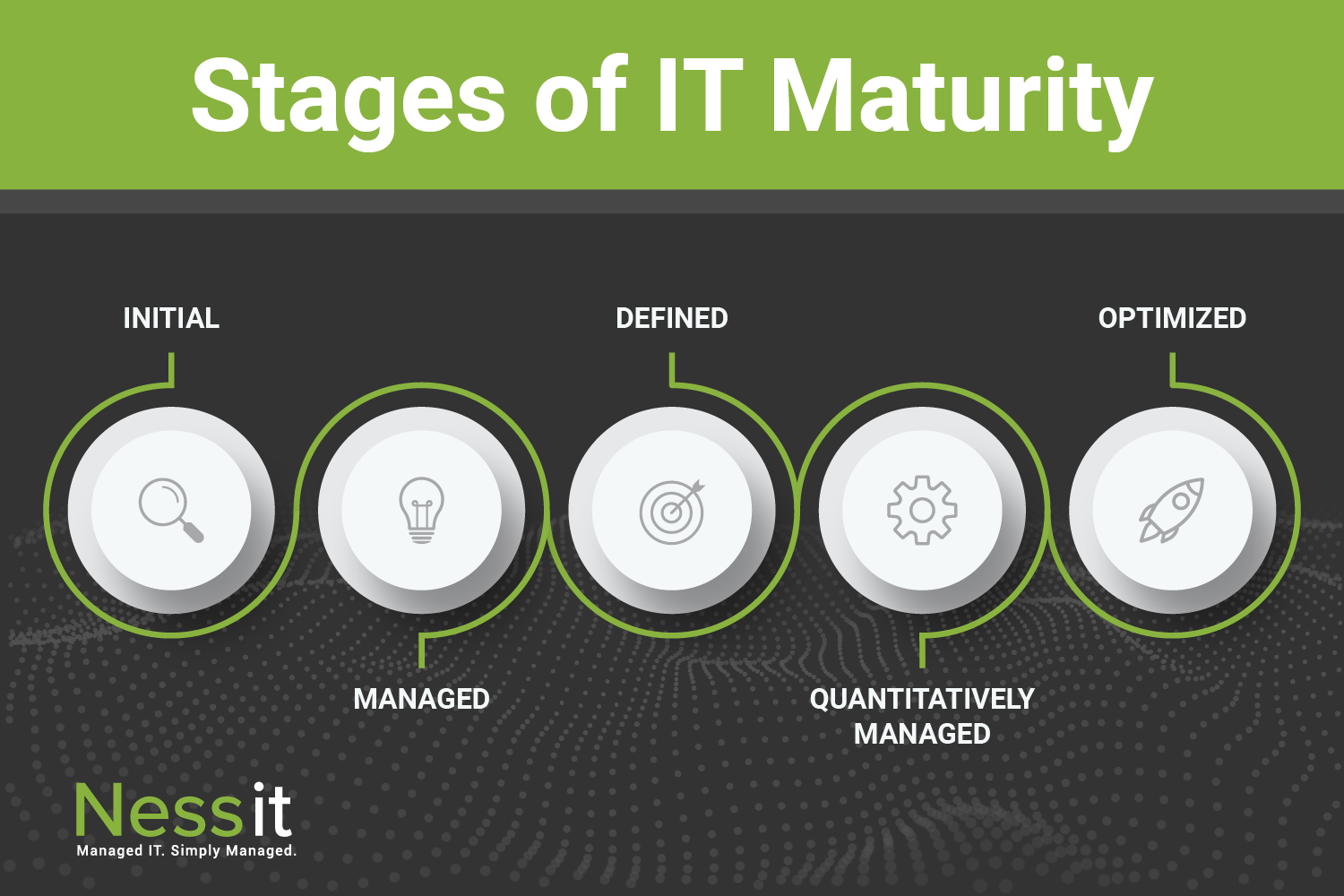
The effectiveness of your IT infrastructure greatly impacts the success of your business. Having basic IT systems in place is not enough. Achieving IT maturity is critical for long-term growth, innovation, and competitive advantage. So, what exactly is IT maturity, why is it important, and how can Nessit help your business get there?
The single most effective way to safeguard your business from cyberattacks is through employee training. Employees can unknowingly become the gateway for cybercriminals by clicking on malicious links, using weak passwords, falling for phishing scams, or accidentally sharing sensitive information that can compromise your entire network. Here’s what you need to know to protect sensitive data and maintain the integrity of your IT infrastructure:
Cybersecurity is a critical component in any organization, large or small. The increasing frequency and evolving nature of threats means that simply installing antivirus software or setting up a firewall isn’t enough. Security is an ongoing process that requires constant vigilance, regular updates, and proactive measures. As a Managed Service Provider (MSP), Nessit understands the complexities of maintaining robust cybersecurity and is dedicated to safeguarding your business.
Achieving peak performance from your IT systems means more than just investing in the latest technology or services. Forward-thinking companies recognize the importance of having a future-proof IT strategy in place, and both co-managed and fully managed IT services can provide an effective solution for your business.
Architectural firms have unique IT needs, and rely on specialized software and applications, large data storage, and seamless connectivity. Employees working in-office and remotely need to be able to access, share, and collaborate on files, blueprints, schematics, and 3D models. Managing your network infrastructure can be a time-consuming and complex task, and unforeseen IT issues can have serious consequences in terms of diminished productivity, disrupted deadlines, data loss, and compromised security.
At Nessit, we take remote readiness extremely seriously. As the IT partner for each of our clients, we are only as successful as our least successful remote team. Having successfully managed this transition to remote work for countless clients and for Nessit itself, we know a thing or two about remote readiness.