Mergers and acquisitions are exciting milestones for an insurance agency. They signal growth, new opportunities, and an expanded customer base. … Read more
IT Consulting
Insurance agencies handle some of the most sensitive data there is, from medical and financial records to social security numbers, … Read more
Collaboration between the public and private sectors is vital when it comes to safeguarding critical U.S. infrastructure, including sectors like … Read more
For municipalities, establishing an effective IT budget is essential for maintaining secure, efficient, and future-ready operations. A well-structured IT budget allows local governments to be proactive–rather than reacting to costly emergencies–and to provide essential services while maximizing available funds.
Municipalities face unique challenges when it comes to managing IT infrastructure. From safeguarding data to maintaining compliance with local and state regulations, effective IT management is necessary to ensure municipal operations run smoothly. Budget restrictions can make it difficult to fully staff an IT department that can meet the complex needs of schools, fire, police, planning, clerks, and more.
When a New Hampshire town became dissatisfied with their longtime IT vendor, they went looking for a second opinion. We were one of three managed service providers to submit a bid with remediation plans, and our bid was selected to become this municipality’s IT vendor. How did we create a custom proposal for their specific IT needs?
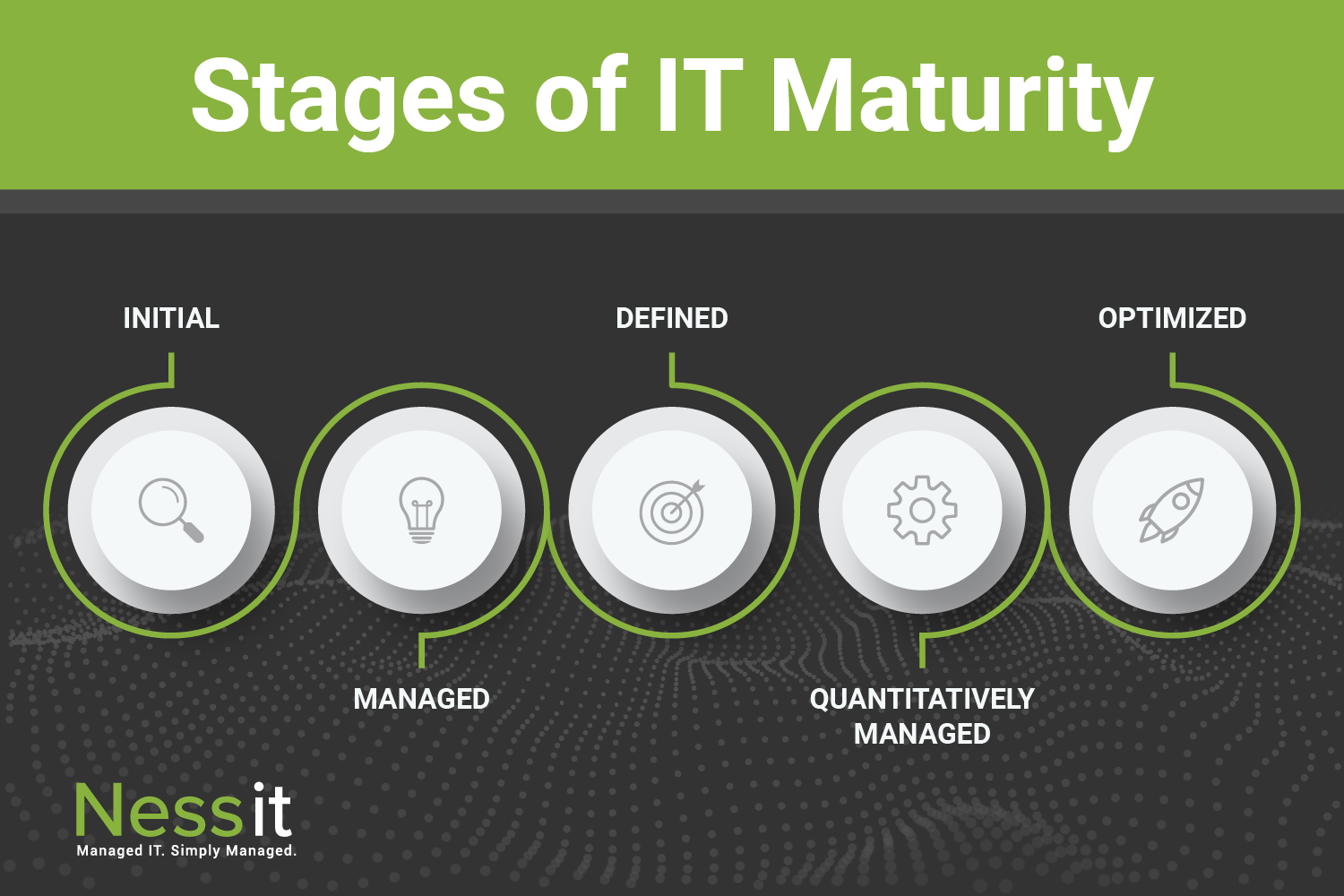
The effectiveness of your IT infrastructure greatly impacts the success of your business. Having basic IT systems in place is not enough. Achieving IT maturity is critical for long-term growth, innovation, and competitive advantage. So, what exactly is IT maturity, why is it important, and how can Nessit help your business get there?
Achieving peak performance from your IT systems means more than just investing in the latest technology or services. Forward-thinking companies recognize the importance of having a future-proof IT strategy in place, and both co-managed and fully managed IT services can provide an effective solution for your business.
Architectural firms have unique IT needs, and rely on specialized software and applications, large data storage, and seamless connectivity. Employees working in-office and remotely need to be able to access, share, and collaborate on files, blueprints, schematics, and 3D models. Managing your network infrastructure can be a time-consuming and complex task, and unforeseen IT issues can have serious consequences in terms of diminished productivity, disrupted deadlines, data loss, and compromised security.