Achieving peak performance from your IT systems means more than just investing in the latest technology or services. Forward-thinking companies recognize the importance of having a future-proof IT strategy in place, and both co-managed and fully managed IT services can provide an effective solution for your business.
 Darci Creative
Darci Creative
Your business relies on digital technology, and as cyberthreats evolve and become more advanced, protecting your data with proactive, robust security measures has never been more important. A data breach can have a catastrophic effect on your company’s finances, productivity, and reputation, and may involve legal repercussions if industry regulations have been violated. Many of the threats businesses need to guard against originate in the internet realm known as the “Dark Web,” a breeding ground for criminal activity and a marketplace for stolen data.
Architectural firms have unique IT needs, and rely on specialized software and applications, large data storage, and seamless connectivity. Employees working in-office and remotely need to be able to access, share, and collaborate on files, blueprints, schematics, and 3D models. Managing your network infrastructure can be a time-consuming and complex task, and unforeseen IT issues can have serious consequences in terms of diminished productivity, disrupted deadlines, data loss, and compromised security.
In this technology-driven landscape, businesses rely on their IT infrastructure to function efficiently and effectively. Organizations large and small face the same complex challenge: how best to maintain IT infrastructure, ensure security, and stay on top of technology trends. The decision comes down to two options: in-house IT teams or managed IT services.
A well thought out IT strategy can be a game-changer, propelling your business to new heights. Conversely, neglecting your IT systems for too long can be a costly mistake, leading to a host of problems, from security vulnerabilities to operational inefficiencies. The good news is that it’s never too late to turn things around.
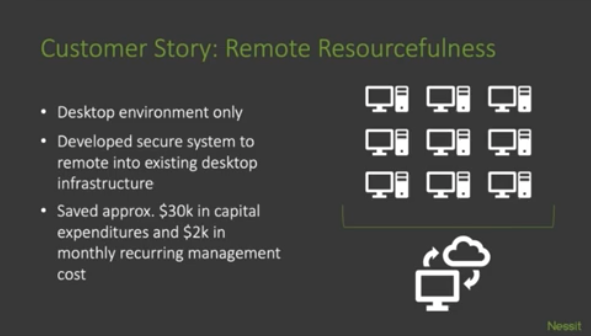
At Nessit, we take remote readiness extremely seriously. As the IT partner for each of our clients, we are only as successful as our least successful remote team. Having successfully managed this transition to remote work for countless clients and for Nessit itself, we know a thing or two about remote readiness.
When it comes to your IT systems and data, having a solid business continuity plan helps you deal with issues when they arise and keeps your business on track. We know most people don’t think about their IT systems on a daily basis (except us) until it breaks down. And when that happens, what do you do?