Remote Readiness in an Evolving Climate
The arrival of our new decade — and the pandemic that came shortly after — changed where and how we all work. That change came far more rapidly than any of us could have imagined. And now, all you have to do is watch the news to see the natural and man-made disasters that can bring a community to a halt. If something happened in your community, would your business be ready?
While the businesses with mature IT systems were able to weather the storm with relative ease, many businesses with less mature IT systems were forced to make drastic changes without being afforded the luxury of time to research and plan for the transition.
As a result, many businesses were effectively forced to overpay for IT solutions that didn’t quite suit their needs.
What is IT Maturity?
IT Maturity is about how effective and efficient a company’s IT systems are in relation to their people, products and processes. A company who follows best practices, understands the full landscape of their IT systems, and regularly invests in their technology would be seen as having mature IT systems.
How To Be Remote Ready
At Nessit, we take remote readiness extremely seriously. As the IT partner for each of our clients, we are only as successful as our least successful remote team. Having successfully managed this transition to remote work for countless clients and even for ourselves, we know a thing or two about remote readiness.
For example, we helped a client with a desktop-only environment develop a mature IT system tailored to their specific needs which would allow for secure remote access into existing desktop infrastructure.
This enabled the client to save ~$30,000 in upfront capital expenditures and a further ~$2,000 per month in recurring management costs. Over the course of the next 5 years, that amounts $150,000 in cost savings for a system that perfectly suited their needs.
Another client had an IT system set up to accommodate team members working onsite from two separate offices. This client had no plans to move towards remote work; as such, they had previously been putting most of their IT budget towards on-premise enhancements.
We were able to help them seamlessly transition to 100% remote work with minimal additional upfront capital expenditures by guiding them towards long-term cloud-based investments in their IT systems to allow for enhanced current and future use.
For those unaccustomed to managing a remote workforce or simply seeking to streamline an immature or bloated incumbent IT solution, preparing for remote work — or even knowing what questions are most important — can seem like a daunting task.
Here are the questions we ask when helping any company find the mature IT solution that best suits their needs for remote work. Asking these questions is a great place to start to ensure your team remains productive, efficient, streamlined, and collaborative, so that your business can weather any storm.
Can I Run My Business Remotely, Today?
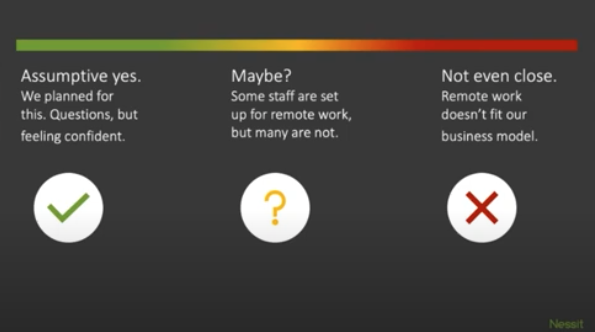
The first question is to determine which of the following three categories your business currently falls within.
- Assumptive Yes: We planned for this! We still have some questions, but are feeling confident.
- Maybe?: Some staff may be able to work remotely, but many are not. We’re not totally sure.
- Not Even Close: Remote work doesn’t fit our business model.
If your organization is a maybe, or a not even close, ask yourself the following questions:
Have I determined which staff members or roles can work remotely, those that can’t work remotely, and those where remote work might be possible with some changes?
These will depend on your business and your employees. There are solutions available that allow for almost anyone to be able to work remotely, but given other business considerations, they may not make sense for you.
Does my team have a plan in place to address systems and equipment needs of employees who may not be set up to work from home? Can employees use their personal computers?
A great rule of thumb here is to refer to your office IT policy. If employees are not currently allowed to use personal devices on the company network, it shouldn’t be allowed at home.
Does my team have a secure, unified video conferencing & collaboration platform to use?
Which functionalities are “nice to haves” and which are “can’t function without it?”
It is important that employees are able to collaborate as easily when remote as they were when it was as simple as popping into a neighboring office. The functionalities your business will need for that may be unique; seeking input from key employees can be very useful here.
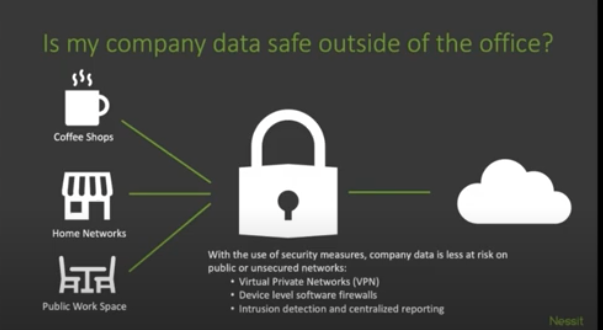
Will my company data be safe outside the office? Have we implemented two-factor authentication for sensitive applications?
Do all devices that will be used remotely have the latest version of their operating software, security software, and line of business applications?
Do my remote employees have access to and know how to use a business grade VPN? Have I purchased enough licenses for all the employees working remotely?
Has my team been educated about being aware of phishing and other attacks that may take place?
Does my company have a plan in place to regularly check in with remote staff to confirm they’re comfortable working remotely and have the tools they need?
Unfortunately, the malevolent actors out there only become more and more sophisticated. It’s important to ensure employees are up to date as well, because the consequences of a breach can be quite severe.
If you are in an industry with higher than usual security requirements, making sure you understand and currently comply with those requirements needs to come first and foremost.
Each organization needs to determine what level of security is right for them in order to adequately protect company data when employees access it and work on their home WiFi, in coffee shops, and in public workspaces.
For some organizations, Virtual Private Networks, or VPNs, are a sufficient solution when paired with two-factor authentication. Other organizations with more stringent security requirements may need device level software firewalls and/or intrusion detection and centralized reporting.
Have I ensured there are backups of our servers so staff can keep working when extra network traffic causes primary servers to go down? Do employees know where to backup data to ensure business continuity in the event of device failure.
No one ever plans on a network going down or devices failing, but even so, the consequences of not being prepared for these contingencies dwarfs the cost of putting them in place.
Does my company have guidelines in place for remote employees, including proper use of company assets and security guidelines? Does my team know about them?
If you are only beginning the transition to remote work, such guidelines may not be formalized. Formal guidelines will provide employees with clarity about what is and is not acceptable and very well may help preempt major headaches down the road.
Is my IT infrastructure and network designed to handle increased remote traffic?
While your network may seem to be working just fine when everyone is onsite, changes in the demand placed on your network by a remote workforce can impact the overall functionality of your network.
For example, when everyone is in the office, there are no restrictions on download or upload speeds. But for remote employees, the best possible download speed becomes limited to the speed of an office file upload.
Even if fractional differences in speed don’t seem that significant, employees cannot possibly be as efficient as they could be if they are constantly waiting for things to load.
That can be exacerbated when there are numerous programs running that occupy significant RAM. If an employee has Zoom, Teams, Excel, and other role-specific software constantly running, that employee may be spending a lot more time twiddling their thumbs than we’d like to realize.

Have I reviewed and confirmed that existing policies and customer agreements allow us to work remotely when feasible, prudent, and contractually admissible?
So, are you Remote Ready?
Download our checklist to share with your team.
